One thing I have become notorious for as an editor is nagging pentesters to sort any lists contained within a report, especially lists of IP addresses. Worse, for IPv4 addresses, I insist that they be sorted by octet. (IPv6 addresses still are not common enough for the matter to ever come up.) Some testers get it. Others don’t and think I truly am OCD and that I’m making a mountain out of a molehill. So be it. This is a hill I am willing to fight to defend. Dying for it seems a bit extreme, but I hope it won’t come to that.
The reason I am so adamant about this issue in particular is because I have been on the receiving end of long lists of IP addresses for servers that had to be checked individually for configuration and/or content changes. Trust me when I say that going through a long list of servers is a PITA of the first water, and if the list of server names and/or locations is disorganized and random, a job that is mind-numbing at best becomes both mind-numbing AND infuriating. The poor schmoe on the receiving end of a list of servers that needs to be patched, updated, or have their config tweaked is more likely to curse you and your family for the next seven generations if you hand them a random mess than if you hand them a list that is well sorted, organized, and tidy.
To help illustrate precisely what I mean, let’s take a look at a simple list of words, sorted two different ways: randomly, and alphabetically. Look at these lists and tell me which list is easier to read, recognize, and comprehend.

These two lists contain exactly the same words, but the one on the left is randomized, disorderly, and chaotic. The one on the right flows sequentially, each word in alphabetical order. If you were receiving a report that you paid good money for, which of these two lists would reflect better on the person(s) who wrote it? Whose feedback would you consider to be more reliable and accurate?
Now let’s to the same thing with a list of 15 IPv4 addresses. The image below is a screenshot taken from a Word document demonstrating all the different ways that Microsoft Word knows to sort a list of numbers.
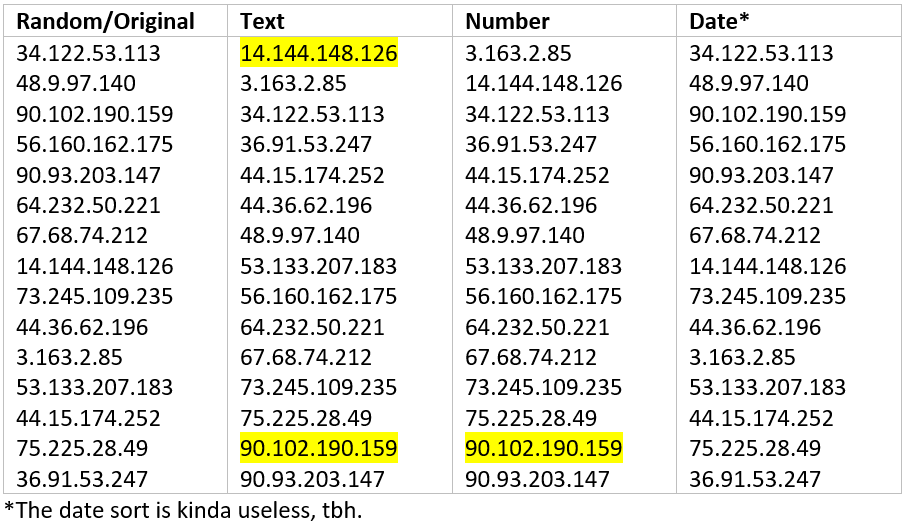
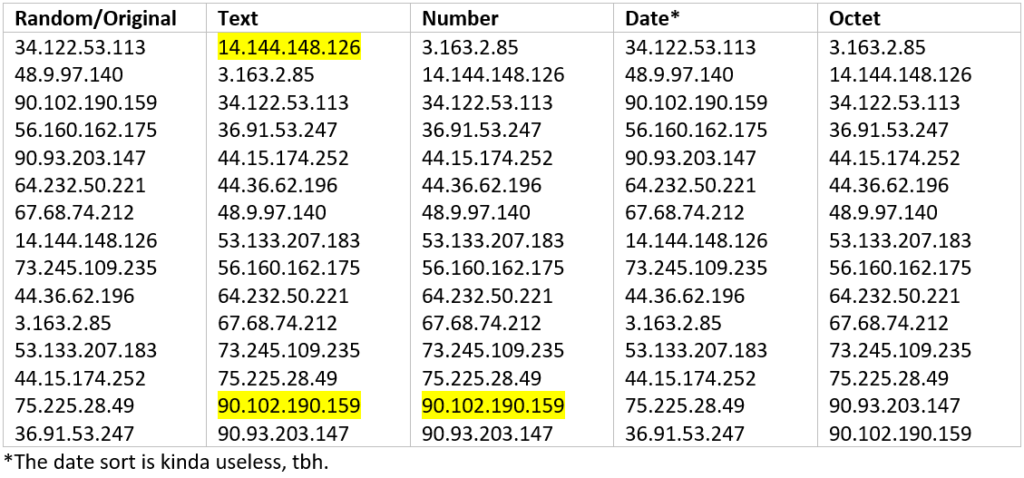
As you can see, Word tried hard, and sometimes comes close, but in the end fails miserably when it comes to sorting IP addresses by octet. The date sort was a complete fail, and both the text and number sorts left at least one of our sample IP addresses out of order, shown by the highlighted numbers. Fortunately, every single pentester I know is adept at working within various flavors of the Linux operating system. It just so happens that there are some very simple and easy commands that will solve this problem with a minimum of effort.
One possible option is:
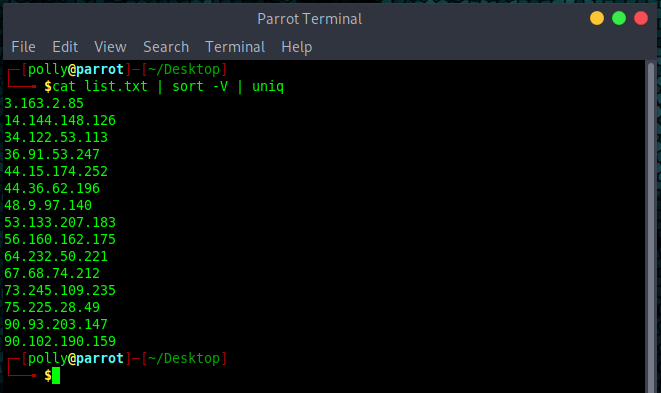
cat list.txt | sort -V | uniqIn this particular code snippet, the cat command throws the contents of list.txt onto the screen, sort performs the sorting action using the -V switch which, while intended to be used for version numbers, can also be used for IPv4 addresses. Lastly, uniq makes sure that any duplicates are ignored.
Or perhaps this is more your style:
sort -uV list.txt > sorted_list.txtIn this instance, sort is being executed directly on the list.txt file and will send the results to a separate file. The -uV switch makes sure all values are unique and sorted as if they were version numbers. Again, this is not the intended use of the -V option, but since when do hackers care about what was intended, anyway?
Either way, start with the sort command and pipe in whatever options you want.
You may have also noticed that both of the sample commands above include something to remove duplicate addresses. This is another good practice for testers to incorporate into their methodology. By removing duplicate values in their lists, the accuracy of list counts will improve. Few things will kill your cred as quickly as typos and miscounts. Once the client sees a typo, or finds out that a count contained in a finding was incorrect, everything else in that report becomes suspect. That throws shade on the tester, their company, and everything they state in their analyses.
Hopefully, you now see why I am so adamant about sorting lists of items, and why it matters to anyone receiving a pentest report. Sorting lists of IP addresses is trivially easy for anyone rocking a command line interface, and the potential for lessening pain and frustration for the IT folks who have to actually do the work to mitigate vulns makes it even more aggravating when testers push back when I ask them to do so.
At the end of the day, why would we, as cybersecurity professionals, want to inflict more pain and suffering on the very people we are supposed to be helping? Sorting your lists is an easy win, and will reduce the aggravation levels of people taking action based on our findings.